Malware (short for malicious software) is any software designed to cause damage to or spy on a computer, server, client, or computer network for the benefit of some third party. The most common types of malware are: viruses, worms, Trojan horses, ransomware, spyware, adware, rootkits and keyloggers.
Malware exploits security defects (security bugs or vulnerabilities) in the design of the operating system, in applications such as browsers, or in vulnerable versions of browser plugins such as Adobe Flash Player, Adobe Acrobat or Reader, or Java SE.
Malware authors exploit software security defects such as bugs or vulnerabilities. Some closed source operating systems feature deliberate back-doors that may be exploited by attackers.
What is Ransomware?
Ransomware is malware that encrypts files on an infected computer, then demands payment in exchange for the decryption key. In the majority of cases the infected computer is running a Microsoft Windows operating system.
Ransomware attacks are typically carried out using a Trojan that is presented as a legitimate file that the user is tricked into downloading or opening when received as an email attachment.
The tricky part of getting your files back is not just having to pay for the ransom, but getting the ransomware authors to honour their promise by decrypting the files. As of October 2013, a strain of ransomware called Cryptolocker was infecting around 150,000 computers each month. In a period of nine months, it is thought to have generated about $3 million in ransom payments.
How to protect yourself from Ransomware?
- Keep your system up-to-date - Install all security updates from trusted sources for operating system, applications and third-party device drivers.
- Develop a good cyber hygiene - Be cautious when opening e-mail attachments and links.
- Design network separation - Keep critical computers isolated from networks.
- Implement a good backup system - To be able to restore all encrypted files after an ransomware attack, you must have at least one file version backup up that is not affected by the ransomware attack.
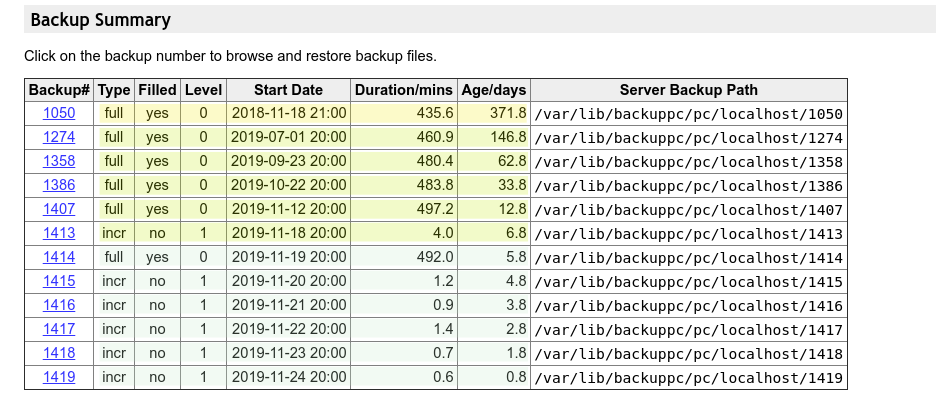
Our Backup Server Solution offers you possibility to restore your lost files from multiple restore points in the past.
This example has 12 possible restore points of different ages, ordered from oldest (371.8 days) to the newest (less than 1 day old):