Debian is the preferred choice of an operating system for all our IT Solutions for Small Business and Home users.
Debian is a free operating system (OS) for your computer. An operating system is the set of basic programs and utilities that make your computer run. Debian provides more than a pure OS: it comes with over 59000 packages, precompiled software bundled up in a nice format for easy installation on your machine. Read more about Debian ...
Debian is under continual development. The latest release is Debian 11.3. It is also (currently) known as stable or by its codename "Bullseye". Each version also corresponds to a set of named software repositories (at least one per CPU architecture).
At any given time, there is one stable release of Debian, which has the support of the Debian security team. When a new stable version is released, the security team will usually cover the previous version for a year or so, while they also cover the new/current version. Only stable is recommended for production use.
There are also two main development repositories unstable and testing which are continually updated during the development of the next stable release. The latest packages arrive in unstable (which always has the codename "Sid"). Packages are automatically copied from unstable to testing when they meet criteria such as lack of release-critical bugs, and dependencies being satisfied by other packages in testing.
Debian Long Term Support (LTS) is a project to extend the lifetime of all Debian stable releases to (at least) 5 years. Debian LTS is not handled by the Debian security team, but by a separate group of volunteers and companies interested in making it a success.
Thus the Debian LTS team takes over security maintenance of the various releases once the Debian Security team stops its work. Read more about Debian Long Term Support here.
Extended Long Term Support (ELTS) is a commercial offering to further extend the lifetime of Debian releases (after the 5 years offered by the LTS project). It is not an official Debian project. Debian's infrastructure and other Debian resources are not involved. Read more about Debian Extended Long Term Support here.
Debian release timeline
| Version | Code Name | Release Date | EOL | EOL LTS | EOL ELTS |
|---|---|---|---|---|---|
| 12 | Bookworm | ||||
| 11 | Bullseye | 14-08-2021 | |||
| 10 | Buster | 06-07-2019 | ~08-2022 | ||
| 9 | Stretch | 17-06-2017 | 06-07-2020 | 30-06-2022 | |
| 8 | Jessie | 25-04-2015 | 17-06-2018 | 30-06-2020 | ~30-06-2022 |
| 7 | Wheezy | 04-05-2013 | 25-04-2016 | 31-05-2018 | ~30-06-2020 |
Note: Only Debian versions with the current Standard, Long Term Support (LTS) or Extended Long Term Support (ELTS) are included in this timeline.
Servers are working around the clock doing their job as expected. But like any machine they do require some attention and maintenance to prevent server disastrous failures and data loss. An important part of the server maintenance is server monitoring performed by system administrators to ensure that the server is performing as expected and all problems are discovered and solved before they become serious.
Server monitoring can be done using either manual techniques or automated server monitoring software tools. Even if you are responsible for only 1 server, you will very soon realise that you need a monitoring tool. Yes, we humans need some healthy night sleep.
It is important for a system monitoring tool to just work - all the time, and you should be able to trust it to do so. A system monitoring tool needs to be non-intrusive and you should be able to forget about it once it's installed.
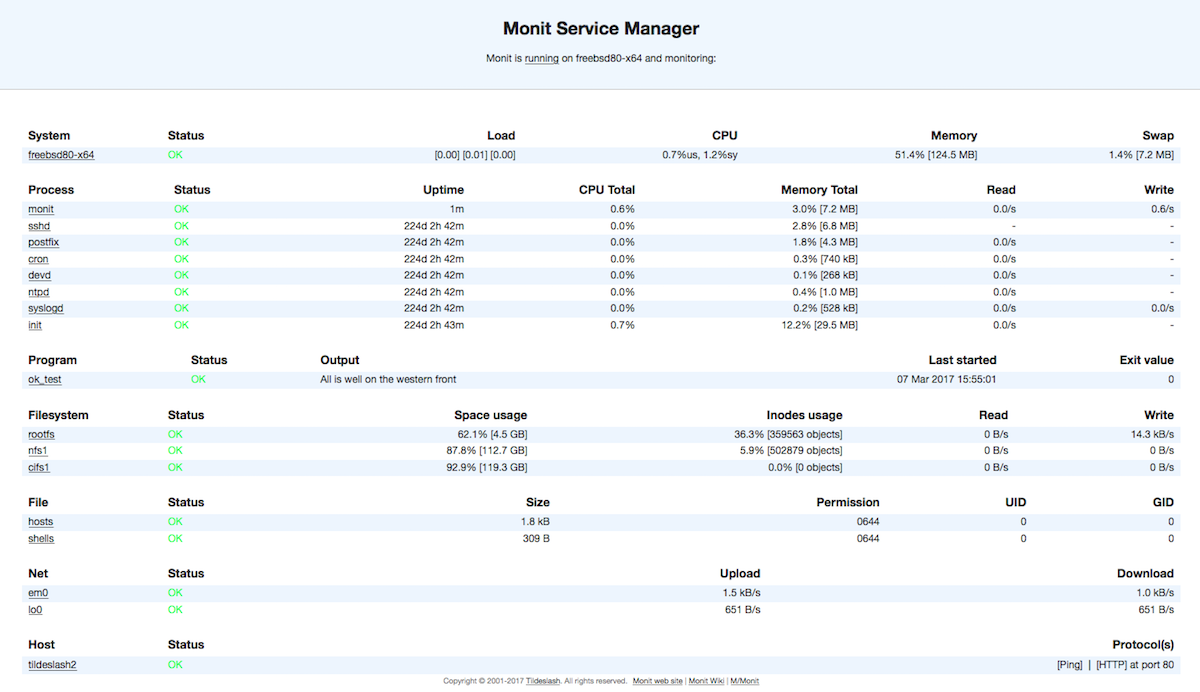
Our server monitoring tool of choice is the MONIT ( https://mmonit.com/monit/ ). Monit is a small Open Source utility for managing and monitoring Unix systems. Monit conducts automatic maintenance and repair and can execute meaningful causal actions in error situations.
That's what is exciting about Monit. Monit is more than just a passive monitoring tool. Suppose in the middle of the night apache is using too much resources (e.g. if a DoS attack is in progress) Monit can stop or restart apache and send you an alert message.
Monit Features
- Proactive: Monit can act if an error situation should occur, e.g. if Exim is not running, Monit can start it again and send you an alert.
- Monitoring daemon processes: Monit is particularly useful for monitoring daemon processes, such as those started at system boot time from /etc/init/ For instance postfix, sshd, apache, mysql, fail2ban, etc.
- Monitoring Files, Dirs and Filesystems: Monit can monitor these items for changes, such as timestamps changes, checksum changes or size changes. This is also useful for security reasons - you can monitor the md5 or sha1 checksum of files that should not change and get an alert or perform an action if they should change.
- Monitoring Network Connections: Network tests can be performed on a protocol level; Monit has built-in tests for the main Internet protocols, such as HTTP, SMTP etc. Even if a protocol is not supported you can still test the server as you can configure Monit to send any data and test the response from the server.
- Monitoring Programs and scripts: With Monit you can test programs or scripts at certain times, much like cron, but in addition, you can test the exit value of a program and perform an action or send an alert if the exit value indicates an error. This means that you can use Monit to perform any type of check you can write a script for.
- Monitoring General System Resources: Finally, Monit can be used to monitor general system resources on localhost such as overall CPU usage, Memory and Load Average.
- Built-in a lightweight HTTP(S) interface: You can use it to browse the Monit server and check the status of all monitored services. From the web-interface you can start, stop and restart processes and disable or enable monitoring of services.
Web Interface
Logging and Alerts
Monit can logging status and error messages to a file or via syslog. We are using dedicated Monit log file in our Debian based systems ( /var/log/monit.log ).
If an event occurs Monit will raise an alert. By default, Monit only sends alert notifications via email. Additionally, a script can be added to send alerts using other means. In our solutions we are using a customised Monit2Telegram script to send Monit alerts to Telegram messenger using a Telegram bot.
Links
Malware (short for malicious software) is any software designed to cause damage to or spy on a computer, server, client, or computer network for the benefit of some third party. The most common types of malware are: viruses, worms, Trojan horses, ransomware, spyware, adware, rootkits and keyloggers.
Malware exploits security defects (security bugs or vulnerabilities) in the design of the operating system, in applications such as browsers, or in vulnerable versions of browser plugins such as Adobe Flash Player, Adobe Acrobat or Reader, or Java SE.
Malware authors exploit software security defects such as bugs or vulnerabilities. Some closed source operating systems feature deliberate back-doors that may be exploited by attackers.
What is Ransomware?
Ransomware is malware that encrypts files on an infected computer, then demands payment in exchange for the decryption key. In the majority of cases the infected computer is running a Microsoft Windows operating system.
Ransomware attacks are typically carried out using a Trojan that is presented as a legitimate file that the user is tricked into downloading or opening when received as an email attachment.
The tricky part of getting your files back is not just having to pay for the ransom, but getting the ransomware authors to honour their promise by decrypting the files. As of October 2013, a strain of ransomware called Cryptolocker was infecting around 150,000 computers each month. In a period of nine months, it is thought to have generated about $3 million in ransom payments.
How to protect yourself from Ransomware?
- Keep your system up-to-date - Install all security updates from trusted sources for operating system, applications and third-party device drivers.
- Develop a good cyber hygiene - Be cautious when opening e-mail attachments and links.
- Design network separation - Keep critical computers isolated from networks.
- Implement a good backup system - To be able to restore all encrypted files after an ransomware attack, you must have at least one file version backup up that is not affected by the ransomware attack.
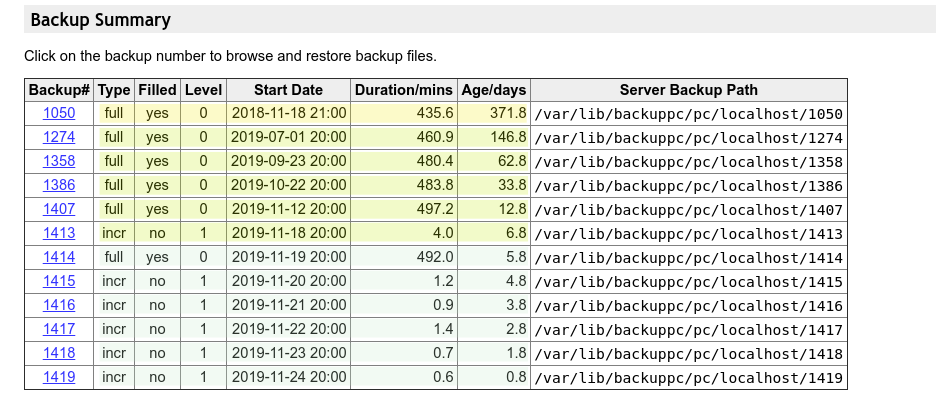
Our Backup Server Solution offers you possibility to restore your lost files from multiple restore points in the past.
This example has 12 possible restore points of different ages, ordered from oldest (371.8 days) to the newest (less than 1 day old):
"Source code" is a computer program in its original, human readable form written in a computer programming language. To be executable this source code must be translated (compiled or interpreted) into non-human readable, computer machine code, also called object code.
The majority of end users never see the source code of programs that they run on their computers. Thus they are not able to see what these programs are doing on their computers or how their personal data is used by these programs.
Most likely you have heard or read about the terms Free Software, Proprietary Software, Open Source Software, Closed Source Software, Shareware, Freeware, etc. But what do all these terms mean? How are they different from one another, and what implications do these differences have to the security and privacy of your computers and personal data?
What is Free Software?
The creators/founders of the GNU Project - Free Software Foundation explain that:
“Free software” means software that respects users' freedom and community. Roughly, it means that the users have the freedom to run, copy, distribute, study, change and improve the software. Thus, “free software” is a matter of liberty, not price. To understand the concept, you should think of “free” as in “free speech,” not as in “free beer”. We sometimes call it “libre software,” borrowing the French or Spanish word for “free” as in freedom, to show we do not mean the software is gratis.
We campaign for these freedoms because everyone deserves them. With these freedoms, the users (both individually and collectively) control the program and what it does for them. When users don't control the program, we call it a “non-free” or “proprietary” program. The nonfree program controls the users, and the developer controls the program; this makes the program an instrument of unjust power.
What is Proprietary Software?
Proprietary software, also called closed-source software, is a non-free computer software for which the developer or owner retains intellectual property rights exclusively.
Only the original owner of the software is legally allowed to view and modify the source code. Users of proprietary software must unconditionally trust them that there is no malicious code running on their computers and misusing their data.
A proprietary program puts its developers or owner in a position of power over its users. This power is in itself an injustice. The initial injustice of proprietary software often leads to further injustices: Malicious functionalities.
Some examples of malicious functionalities:
- Back doors: Any feature of a program that enables someone who is not supposed to be in control of the computer to send it commands. Examples: Spying, altering users data or settings, installing, deleting or disabling other programs.
- Digital Rights Management, or “DRM”: Functionalities designed to restrict what users can or can’t do with the data on their computers.
- Proprietary Incompatibility of a program with third party software that operates on the same data types. A fairly common sort of incompatibility is the use of secret formats or protocols. This directly blocks or hinders users from switching to any other program and, in particular, from switching to free software which can liberate the device the software runs on.
- Proprietary Surveillance: Collecting user data and sharing it with third parties.
- Proprietary Tethers: Tethering a product or program means designing it to work only by communicating with a specific server. That is always an injustice since it means you can't use the program without a connection to that server. It is also a secondary injustice if you can't communicate with the server in an alternative way. In some cases, tethering is used to do specific nasty things to the users: eBooks “bought” from Microsoft's store check that their DRM is valid by connecting to the store every time their “owner” wants to read them. When Microsoft closes this store, it will brick all DRM'ed eBooks it has ever “sold” unless they become generous enough to deactivate this aspect of the DRM code.
What is Freeware?
Freeware is closed source software available free of charge. ZERO $, but you aren't allowed to know exactly what this program, running on your computer is really doing with your data.
Examples:
- Adobe PDF Reader
- Kik Messenger
- Google Chrome
What is Shareware?
Shareware is proprietary closed source software distributed free of charge to users, either with limited features or on a time limited trial basis. To use it after the time limit, you have to pay for the software.
Shareware limitation examples:
- Adware - Contains ads for generating revenue to developers
- Donationware - Offers optional payment option
- Nagware - Often begs users to pay for a licence to continue using the program
- Demoware - A feature limited demonstration version of the software
What is Open Source Software?
People very often confuse open source with free software. They are close, but not interchangeable. All Free Software is Open Source Software, but not all Open Source Software is Free Software.
Open source means you can see the source code, but without the free software aspect there can be restrictions on how you use the source code. Open source developers may let you look at the source code, but you may not be allowed to actually run binaries that are compiled from it: Look but don't touch, and don't run. You may also be allowed to build binaries, but only with limited features. Finally, and most important in practice, many products containing computers check signatures on their executable programs to block users from installing different executables; only privileged companies can make executables that can run on the device, or can access its full capabilities.
Many Android products contain non-free executables of Linux, even though its source code is under GNU GPL version 2.
The criteria for open source without the free software aspect are concerned solely with the licensing of the source code. Thus you can end up with non-free executables that was compiled from free and open source code.
In Conclusion:
Only Free Software gives users (not just the developer) ultimate control over the software and, subsequently, over their devices and data.
Here you'll find the most recent and useful information about IT solutions and services for personal and small business users.
Covering a range of IT topics with a focus on security and privacy of IT solutions for small business, we aim to help you to select the most appropriate custom IT solutions to satisfy your small business needs.